Generate Cert Pem Key Pem
OVERVIEW
/ojosoft-total-video-converter-key-generator.html. Zen Load Balancer is able to manage HTTPS connections (HTTP Profile), so the system administrator must to create their own certificates (self-signed certificates) or to acquire Signed Certificates by a Certificate Authority, in both cases the certificate must to be built in PEM format.
Question: Tag: php,sockets,apple-push-notifications,ssl-certificate,apns-php I am trying to create the server side connection for apple push notifications. First, I ask from the user (who probably will be an ios dev) to give the.cer and.p12 files that Apple provides in order to make it a.pem file. Save the combined file as yourdomainname.pem. The.pem file is now ready to use. How to Create a.pem file with the Private Key and Entire Trust Chain. Login into your SSL Certificate Management Console and download your Intermediate (YourCA.crt) and Primary Certificates (yourdomainname.crt). Openssl x509 -in certFileName.cer -outform PEM -out convertedCertFileName.pem. Finally, we’ve the Private Key, the Certificate issued, the Intermediate Certificate and the Root CA Certificate. All these file contents should be combined to create the PEM file in UNIX format. GENERATE CERTIFICATE IN PEM FORMAT. The.pem file is now ready to use. How to Create a.pem file with the Private Key and Entire Trust Chain Login into your SSL Certificate Management Console and download your Intermediate (YourCA.crt) and Primary Certificates (yourdomainname.crt). Hey, complete beginner here just want to confirm I am doing the right thing. I wanted to generate a. Key.pem certificate.pem for my https server using node.js. Is this command correct? Openssl req -newkey rsa:2048 -new -nodes -keyout key.pem -out csr.pem. The tutorial I'm following to create and sign certificates bounces between creating.key and.key.pem files with the -keyout option. For example: master-ca.key.pem and openvpn-ica.key and again vpn-server.key.pem. Does it matter and is there a standard? Jan 21, 2020 PEM certificate can contain both the certificate and the certificate private key in the same file. The PEM certificates are encoded in the text ASCII Base64 format, and you can view them in any text editor. Apache, Nginx and similar web servers are use the SSL certificates in the PEM file format.
The Secure Certificate must be created without password and the keys and CSR must be generated in the server to be secured.
Positives SSL are ready to go in PEM format but Rapid SSL needs to be converted as each file contains the cert, the intermediate CA and the root CA separated.
REQUIREMENTS
The package openssl should be installed in order to generate the keys in the server, in our case will be the Zen Load Balancer instance which should be already installed.
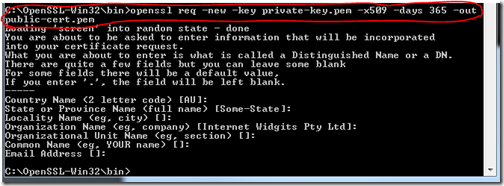
First, generate the key without passphrase.
Then, generate the Certificate Signed Request (.csr) using the generated key (.key) as input.
Once the certificate and intermediate CA files are delivered, ensure to get the issuer root certificate.
All separated files need to be in PEM format: Server Certificate, Intermediate Certificate and Root CA Certificate. If it isn’t, convert the file with the following command:
Finally, we’ve the Private Key, the Certificate issued, the Intermediate Certificate and the Root CA Certificate. All these file contents should be combined to create the PEM file in UNIX format.
GENERATE CERTIFICATE IN PEM FORMAT
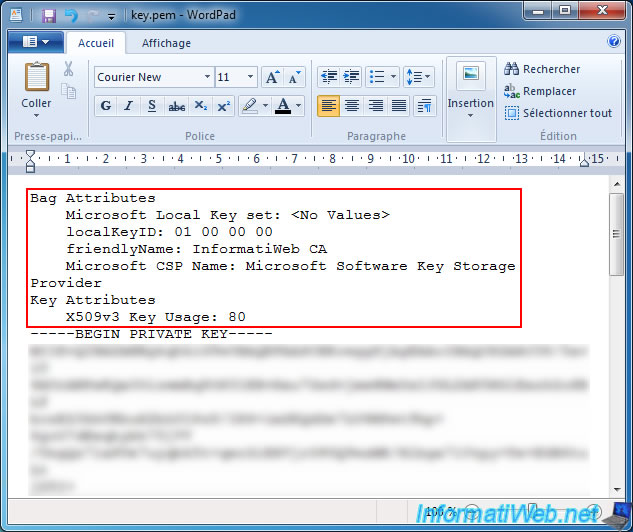
The PEM certificate must to be built with the following structure.
To create a correct PEM structure, it’s needed to concatenate the different file contents generated in the step above with the separations:
It’s mandatory to convert the PEM entire file in UNIX format.
It’s available the certificate named zencert.pem for testing purposes in order to be used with HTTPS profile farms.
6.3.7 Creating SSL Certificates and Keys Using openssl
This section describes how to use the openssl command to set up SSL certificate and key files for use by MySQL servers and clients. The first example shows a simplified procedure such as you might use from the command line. The second shows a script that contains more detail. The first two examples are intended for use on Unix and both use the openssl command that is part of OpenSSL. The third example describes how to set up SSL files on Windows.
Whatever method you use to generate the certificate and key files, the Common Name value used for the server and client certificates/keys must each differ from the Common Name value used for the CA certificate. Otherwise, the certificate and key files will not work for servers compiled using OpenSSL. A typical error in this case is:
Example 1: Creating SSL Files from the Command Line on Unix
The following example shows a set of commands to create MySQL server and client certificate and key files. You will need to respond to several prompts by the openssl commands. To generate test files, you can press Enter to all prompts. To generate files for production use, you should provide nonempty responses.
After generating the certificates, verify them:
Now you have a set of files that can be used as follows:
ca.pem: Use this as the argument to--ssl-caon the server and client sides. (The CA certificate, if used, must be the same on both sides.)server-cert.pem,server-key.pem: Use these as the arguments to--ssl-certand--ssl-keyon the server side.client-cert.pem,client-key.pem: Use these as the arguments to--ssl-certand--ssl-keyon the client side.
To use the files for SSL connections, see Section 6.3.6.4, “Configuring MySQL to Use Secure Connections”.
Example 2: Creating SSL Files Using a Script on Unix
Here is an example script that shows how to set up SSL certificate and key files for MySQL. After executing the script, use the files for SSL connections as described in Section 6.3.6.4, “Configuring MySQL to Use Secure Connections”.
Example 3: Creating SSL Files on Windows
Download OpenSSL for Windows if it is not installed on your system. An overview of available packages can be seen here:
Choose the Win32 OpenSSL Light or Win64 OpenSSL Light package, depending on your architecture (32-bit or 64-bit). The default installation location will be C:OpenSSL-Win32 or C:OpenSSL-Win64, depending on which package you downloaded. The following instructions assume a default location of C:OpenSSL-Win32. Modify this as necessary if you are using the 64-bit package.
If a message occurs during setup indicating '..critical component is missing: Microsoft Visual C++ 2008 Redistributables', cancel the setup and download one of the following packages as well, again depending on your architecture (32-bit or 64-bit):
Visual C++ 2008 Redistributables (x86), available at:
Visual C++ 2008 Redistributables (x64), available at:
After installing the additional package, restart the OpenSSL setup procedure.
During installation, leave the default C:OpenSSL-Win32 as the install path, and also leave the default option 'Copy OpenSSL DLL files to the Windows system directory' selected.
When the installation has finished, add C:OpenSSL-Win32bin to the Windows System Path variable of your server:
On the Windows desktop, right-click the My Computer icon, and select Properties.
Select the Advanced tab from the System Properties menu that appears, and click the button.
Under System Variables, select Path, then click the button. The Edit System Variable dialogue should appear.
Add
';C:OpenSSL-Win32bin'to the end (notice the semicolon).Press OK 3 times.
Check that OpenSSL was correctly integrated into the Path variable by opening a new command console (Start>Run>cmd.exe) and verifying that OpenSSL is available:
Depending on your version of Windows, the preceding path-setting instructions might differ slightly.
Create Cert.pem Key.pem
After OpenSSL has been installed, use instructions similar to those from from Example 1 (shown earlier in this section), with the following changes:
Change the following Unix commands:
On Windows, use these commands instead:
When a
'character is shown at the end of a command line, this'character must be removed and the command lines entered all on a single line.
Generate Cert Pem Key Pem Pdf
After generating the certificate and key files, to use them for SSL connections, see Section 6.3.6.4, “Configuring MySQL to Use Secure Connections”.